Digital Forensics Life Cycle: Digital crimes are rising every year, and cyber security is no longer a topic for experts alone. Schools, small companies, students, and working professionals – everyone today is a digital user. When a cybercrime happens, how do experts track the truth? The answer lies in the digital forensics’ life cycle.
Before we get into the topic, let us first understand what is digital forensics in cyber security and why you should know about it!
Introduction to Digital Forensics
You might have seen digital evidence being used in news or legal cases. But introduction to digital forensics is not only for legal officers or police teams. It is also for common people who want to understand how cybercrime data is examined. digital forensics is like “investigation with proof” in the online world. Whenever a cyber crime happens – whether it is hacking, data leak, online fraud or misuse of a digital device – someone has to trace what really happened, who did it, and how it can be proven. That is where digital forensics plays its role.
So, what is digital forensics in cyber security?
It is the practice of collecting, analysing and presenting electronic data in a structured way so that it can be used as proof. During this training, learners also study the types of digital forensics, including computer, mobile, network and cloud forensics.
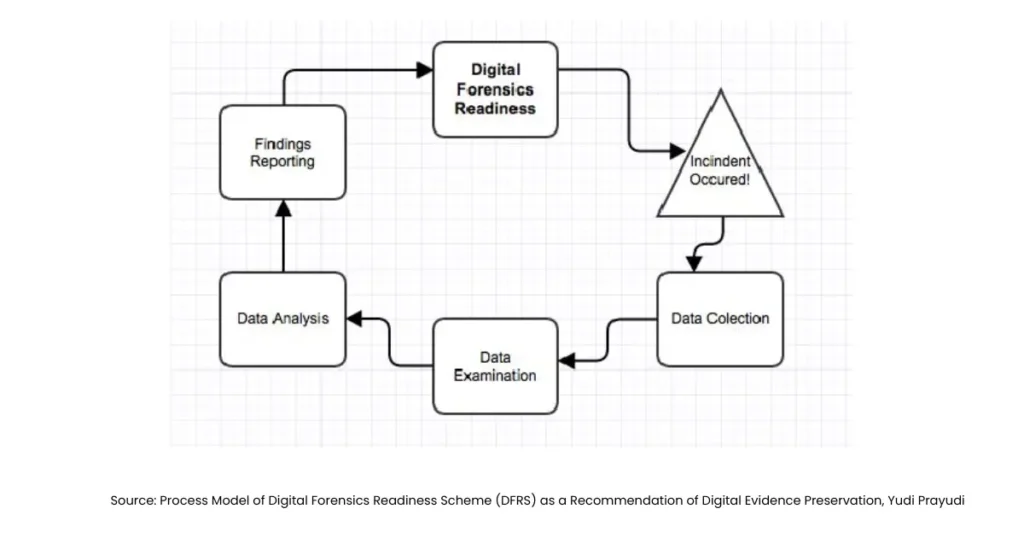
Why Do We Need the Digital Forensics Life Cycle?
Think of a simple situation:
- Someone reports a data theft.
- A digital expert reaches the location.
- The device is collected and locked.
- The data is analysed.
- A report is created.
All of this happens step-by-step because of the digital forensics life cycle. Without this structure, the investigation would lose value. A common saying in forensic training is: “If evidence handling is not recorded, law cannot trust it.”
Stages of the Digital Forensics Life Cycle
The complete cycle usually includes these stages:
- Identification
Detecting what needs to be examined. - Collection and Preservation
Gathering data and protecting it from damage. - Examination
Extracting relevant files and artefacts. - Analysis
Linking the data to events and users. - Documentation and Reporting
Preparing a structured account of findings. - Presentation
Sharing the findings with legal or company authorities.
These stages make it reliable and easy to follow.
Read More: 5 Phases of Ethical Hacking: Can A Hacker Be “Good”?

Role of Chain of Custody
Another very important part of investigation is the chain of custody in digital forensics. This record keeps track of who handled the device or data, at what time, and for what purpose. If the chain is missing, the proof may be questioned in court.
When learners study digital forensics report samples, they clearly see how this chain is mentioned along with timestamps and investigator details.
Community and Learning Perspective In Cyber Security: What You Need To Know
Many young people in India today are exploring cyber security. They start with learning introduction to digital forensics, reading current cases, and reviewing digital forensics report samples. They also try to understand different types of digital forensics to choose the right learning path.
A popular statement from cyber security trainers is: “Forensics is not just about finding what happened, it is about proving it happened.”
This thinking builds awareness and community-level learning.
- It helps experts handle electronic evidence in a proper way.
- Understanding what is digital forensics in cyber security helps students realise its use.
- The chain of custody in digital forensics protects the value of proof.
- Students often refer to digital forensics report samples to learn case format and structure.
- Different types of digital forensics show how wide this field is.
Example of the Digital Forensics Life Cycle
If you are still unsure as to what is this all about, let us simplify it further for you:
Scenario: A company notices that its confidential client files have been leaked. The IT head reports a suspected internal data theft. A digital forensics team is called to investigate.
How the life cycle works in this case:
| Stages | What happens in real life |
|---|---|
| 1. Identification | The team identifies the suspect device – a company laptop used by an employee. Logs show unusual login activity at late night. |
| 2. Collection & Preservation | The laptop is seized and a forensic image (exact copy of the hard disk) is created. The original device is locked and sealed. |
| 3. Examination | The forensic expert checks browser history, deleted files, USB device usage, WhatsApp Web logs, and cloud storage access. |
| 4. Analysis | The investigator finds that the employee used a personal USB drive at 1:52 AM and copied a folder named “Client Financial Data”. Evidence of email forwarding is also recovered. |
| 5. Documentation & Report | All findings are written in a step-by-step report with screenshots, timestamps, and tools used. This is similar to what we see in digital forensics report samples. |
| 6. Presentation | The company management and legal team review the report. Since the chain of custody in digital forensics was properly maintained, the report becomes valid proof for further legal action. |
This is a purely practical example of how it is used in real incidents. It also shows what is digital forensics in cyber security practically and not just theoretically. The same process applies in police investigations, corporate fraud cases, cyber bullying reports, and even hacking complaints.

On A Final Note…
The digital forensics life cycle is not just technical learning. It is a responsible practice that helps society fight digital crime.
When more people understand how digital evidence is collected and stored, they become more aware of safety and legal protection. This awareness slowly builds a stronger and more conscious digital community.
FAQ
It is the step-by-step process of collecting and studying digital evidence.
It means investigating cyber incidents using electronic data as proof.
They include computer, mobile, network, and cloud forensics.
It is the record of who handled the evidence and when.
They are example reports used for learning how cases are documented.





